Navigating the complexities of third-party vendor relationships in today’s digital landscape can feel like a high-stakes balancing act. On one hand, external vendors offer specialized services and efficiencies that are often indispensable for modern businesses to thrive. On the other hand, each new vendor introduces a potential new entry point for security vulnerabilities, making robust due diligence not just a best practice, but an absolute necessity. Understanding who has access to your data, how they protect it, and their overall security posture is paramount to safeguarding your own organization’s integrity.
This is precisely where a well-structured and comprehensive tool becomes invaluable. It serves as your first line of defense, a structured approach to understanding and mitigating the risks associated with outsourcing critical functions or sharing sensitive information. It’s about building trust through transparency, ensuring that your partners meet the security standards you expect and require.
Why a Solid Vendor Security Questionnaire Template is Your Best Friend
In a world where data breaches are increasingly common and the attack surface continues to expand, relying on mere assurances from your vendors just won’t cut it. Imagine a situation where a critical vendor experiences a security incident, and suddenly your own operations are impacted or, worse, your sensitive customer data is exposed. Without proper vetting, you might find yourself in a reactive scramble, trying to understand what happened and how to respond, rather than having a clear understanding of your vendor’s security protocols from the outset.
A well-designed vendor security questionnaire template acts as a systematic framework to gather essential security information from prospective and existing third-party partners. It brings consistency to your vetting process, ensuring that every vendor is evaluated against the same set of critical security controls and practices. This not only saves immense time and effort compared to ad-hoc inquiries but also provides a standardized basis for comparing different vendors and making informed risk assessments.
Furthermore, a comprehensive template helps you identify potential security gaps or areas of concern before an engagement even begins. It shifts your security posture from reactive to proactive, allowing you to address risks, negotiate security clauses in contracts, or even choose alternative vendors if their security practices don’t align with your organization’s risk tolerance. It empowers you to demand a higher level of security from your partners, fostering a more secure supply chain for everyone involved. Ultimately, it’s about building a foundation of shared responsibility and ensuring that security is a non-negotiable part of every vendor relationship.
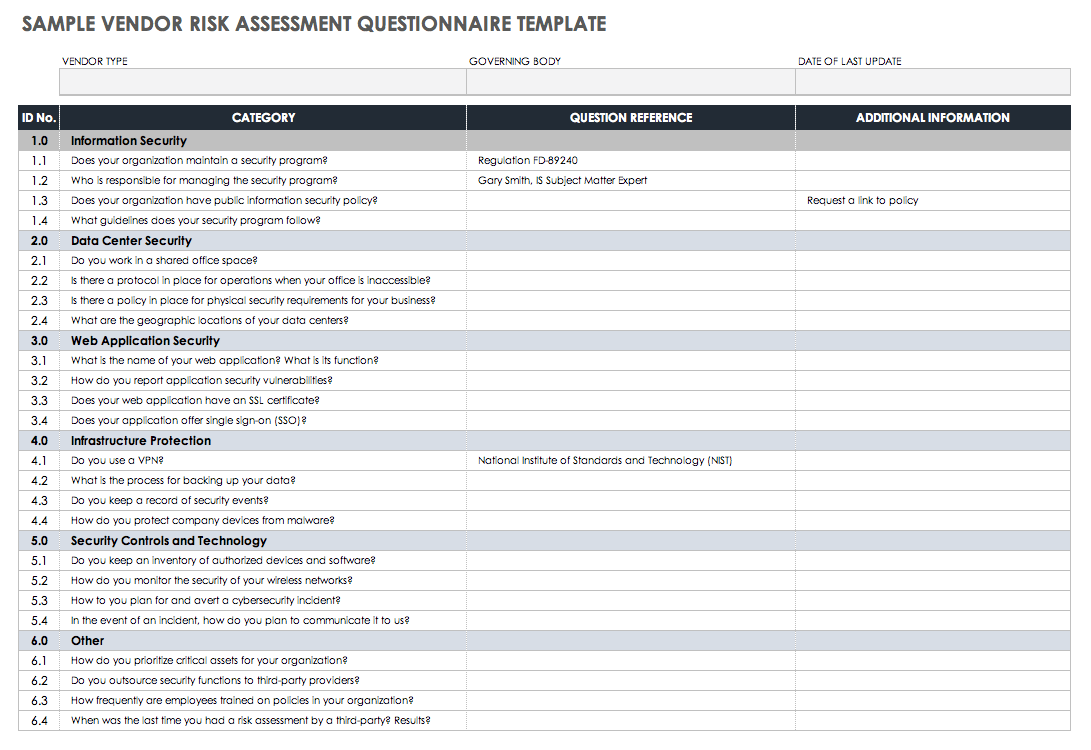
Key Sections to Include in Your Template
A robust vendor security questionnaire template should cover a broad spectrum of security domains to provide a holistic view of a vendor’s posture. Consider including sections that delve deep into their operational security.
- Company and Contact Information: Basic details, emergency contacts.
- Information Security Policies and Procedures: Existence of documented policies, security awareness training, incident response plans.
- Data Encryption and Protection: How data is encrypted (in transit and at rest), data segregation practices.
- Access Control: User authentication methods, least privilege principles, access review processes.
- Network Security: Firewalls, intrusion detection/prevention systems, vulnerability management.
- Application Security: Secure development lifecycle, penetration testing, code review.
- Physical Security: Data center security, visitor access controls.
- Incident Management: Incident reporting, response, and recovery procedures.
- Business Continuity and Disaster Recovery: Backup strategies, recovery time objectives (RTO), recovery point objectives (RPO).
- Compliance and Certifications: Adherence to industry standards (e.g., ISO 27001, SOC 2, HIPAA, GDPR), audit reports.
- Third-Party Risk Management: How the vendor manages their own sub-processors and third parties.
Customizing and Utilizing Your Vendor Security Questionnaire Template Effectively
While a standardized vendor security questionnaire template provides a strong foundation, it’s crucial to remember that one size rarely fits all. The level of detail and specific questions you ask should ideally be tailored to the nature of the vendor relationship and the sensitivity of the data they will handle. A vendor providing janitorial services, for example, might require a different level of scrutiny than a cloud service provider managing your most sensitive customer information. This tiered approach allows you to efficiently allocate your resources, focusing deeper dives on those vendors that pose the highest potential risk to your organization.
Consider segmenting your vendors into risk categories (e.g., high, medium, low) based on factors like the type of data they access, the criticality of the service they provide, or their level of integration with your core systems. For high-risk vendors, you might require more extensive documentation, follow-up calls, or even on-site audits in addition to the questionnaire. For lower-risk vendors, a more concise version of the template might suffice, ensuring that you still cover essential security aspects without overwhelming them or your internal team.
Once the questionnaire is completed and returned by the vendor, the real work begins. It’s not enough to simply collect responses; a thorough review and analysis are paramount. Look for inconsistencies, vague answers, or areas where the vendor’s practices don’t align with your security requirements. Don’t hesitate to ask follow-up questions for clarification or request supporting documentation. This iterative process of inquiry and validation is key to truly understanding a vendor’s security posture and effectively mitigating potential risks.
Integrating the insights gained from your vendor security questionnaire template into your broader risk management framework is also vital. The information should feed into your decision-making processes, contractual agreements, and ongoing vendor management. This ensures that vendor security isn’t a one-off assessment but rather an integral part of your continuous risk monitoring and third-party lifecycle management.
A well-executed vendor security assessment program, driven by a thoughtful questionnaire, significantly strengthens your overall security posture and resilience. It transforms the often-daunting task of third-party risk management into a streamlined, consistent, and actionable process. By investing in a robust approach, organizations can confidently engage with external partners, knowing they have taken proactive steps to protect their valuable assets. This dedication to security ultimately fosters stronger, more trustworthy relationships with vendors and builds greater confidence within your own operations.